As part of a series of posts, we’ll be exploring how Microsoft 365 and Liquidware’s Adaptive Workspace Management suite can complement each other and provide businesses with more productive and secure end users.
Microsoft 365 provides administrators with some great modern tools in order to manage and analyse their end user estate, such as Azure Active Directory, Windows Information Protection and MyAnalytics. Stratusphere UX is able to extend this toolset by providing user experience (UX) reporting and allowing for device assessment. This enables administrators to determine which users are best suited to take on new Microsoft 365 services such as Windows Virtual Desktop and get the most out of your Microsoft licensing.
Today we’ll be looking at how you can leverage Microsoft Intune to deploy the Stratusphere Connector ID Key (CID Key); a lightweight in-guest agent. Traditionally we would leverage application deployment tools such as Microsoft SCCM to provision the CID Key to end points, but in many modern deployments using traditional tools such as SCCM can be both clunky and mean waiting for the device to connect to the corporate network before it gets its applications.
Intune now has the capability to deploy Win32 applications to Windows 10 endpoints that are joined to it via Azure Active Directory, and I’m surprised how many customers I meet that don’t realise it has this functionality. This means that as long as the device has an internet connection, we can deploy the CID Key to it and begin monitoring user experience data as soon as the user logs into their new device for the first time!
Microsoft details how to deploy Win32 applications via Intune through their documentation centre here:
https://docs.microsoft.com/en-us/intune/apps-win32-app-management
We’ll be expanding on those instructions specifically for Stratusphere UX below so you can see just how easy it is.
- Download your UX agent from your Hub. This will ensure that the Hub details are included by default in the CID Key.

- We’ll then need to convert our CID Key .exe into a INTUNEWIN file. Microsoft make this very simple through their Content Prep Tool, which you can download from Github here: https://github.com/Microsoft/Microsoft-Win32-Content-Prep-Tool

- Download the zipped folder, extract and launch the IntuneWinAppUtil application.
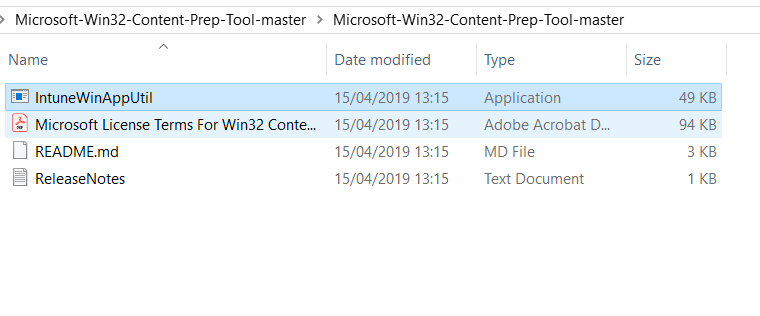
- We will need to fill out the details for where the CID Key .exe is stored, the name of the .exe itself and an output folder that you want the new file to go to. In the example below I’ve made separate folders, but you certainly don’t have to.
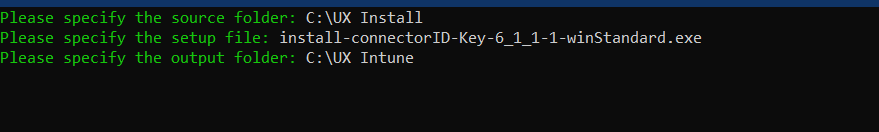
- You will then have an output of an INTUNEWIN file.
- Now we will have to log into your Azure account at https://portal.azure.com and Search for Intune. We are operating under the assumption that you have already done the initial Intune setup steps. If this is you first time using Intune then I recommend following this documentation in order to get started: https://docs.microsoft.com/en-us/intune/free-trial-sign-up
- Once you are ready to go with Intune then select Client Apps in the left hand menu.

- Next is to Select Apps and Add.
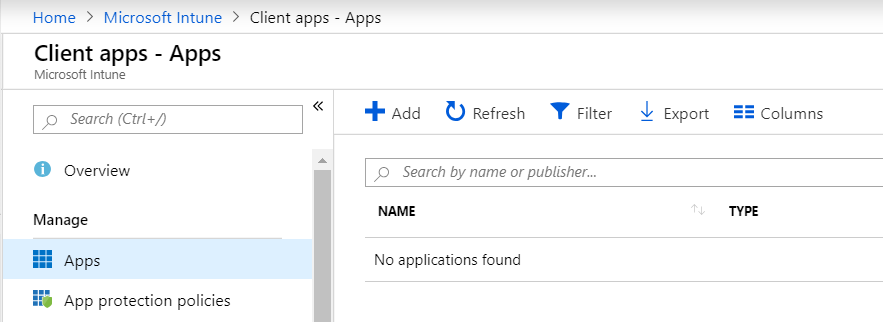
- Choose Win32 from the drop-down menu and select your INTUNEWIN file that we made previously in the App Package File section.
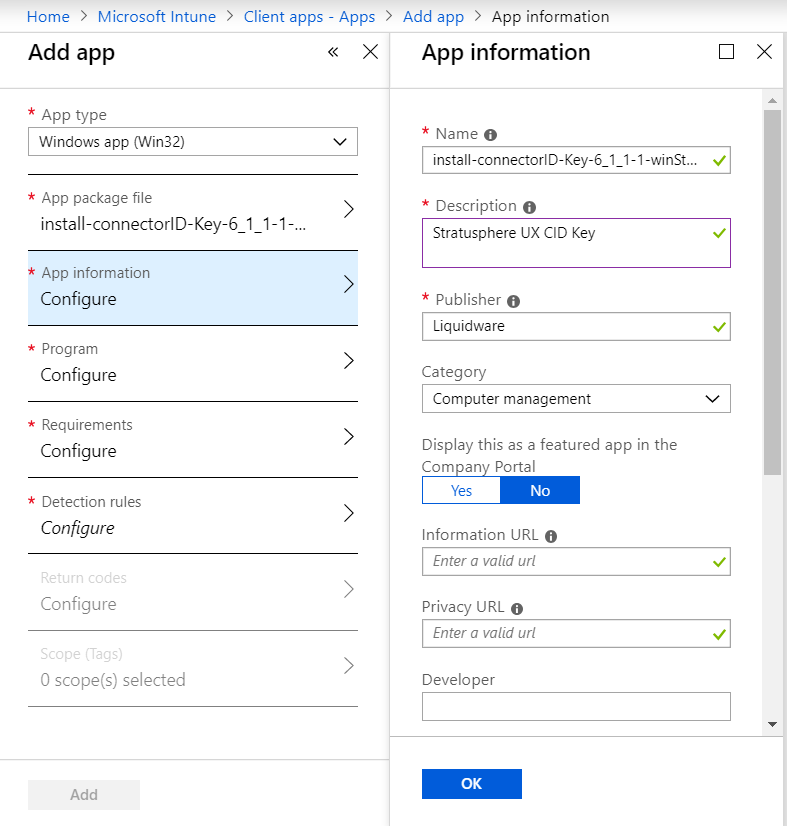
- We then need to fill out the Application Information. You can obviously change the Name here, add a description and the name of the Publisher (Liquidware or LWL). As this is an app we are going to push out, we don’t have to worry about selecting it to be featured in the Company Portal. We’ll also need to add a logo, which I just took from one of my existing Stratusphere UX installs.
- Next in Program set the parameters for installation and uninstallation. Using /s will make CID Key install/uninstall silent so no intervention by the end user is required.

- We then configure the requirements; the CID key is so small that we don’t really need to worry about setting resource requirements. We do have to specify the OS type and minimum OS, but as we work with all versions of Windows 10, this isn’t an issue unless you want to limit which clients receive the agent.

- Finally, we need to set the Detection Rules. There are a lot of ways we can set this; to check a file, a folder, a reg key or even run a custom script. I’ve chosen the simple route of seeing if the CID Key application is in its normal Program Files folder.
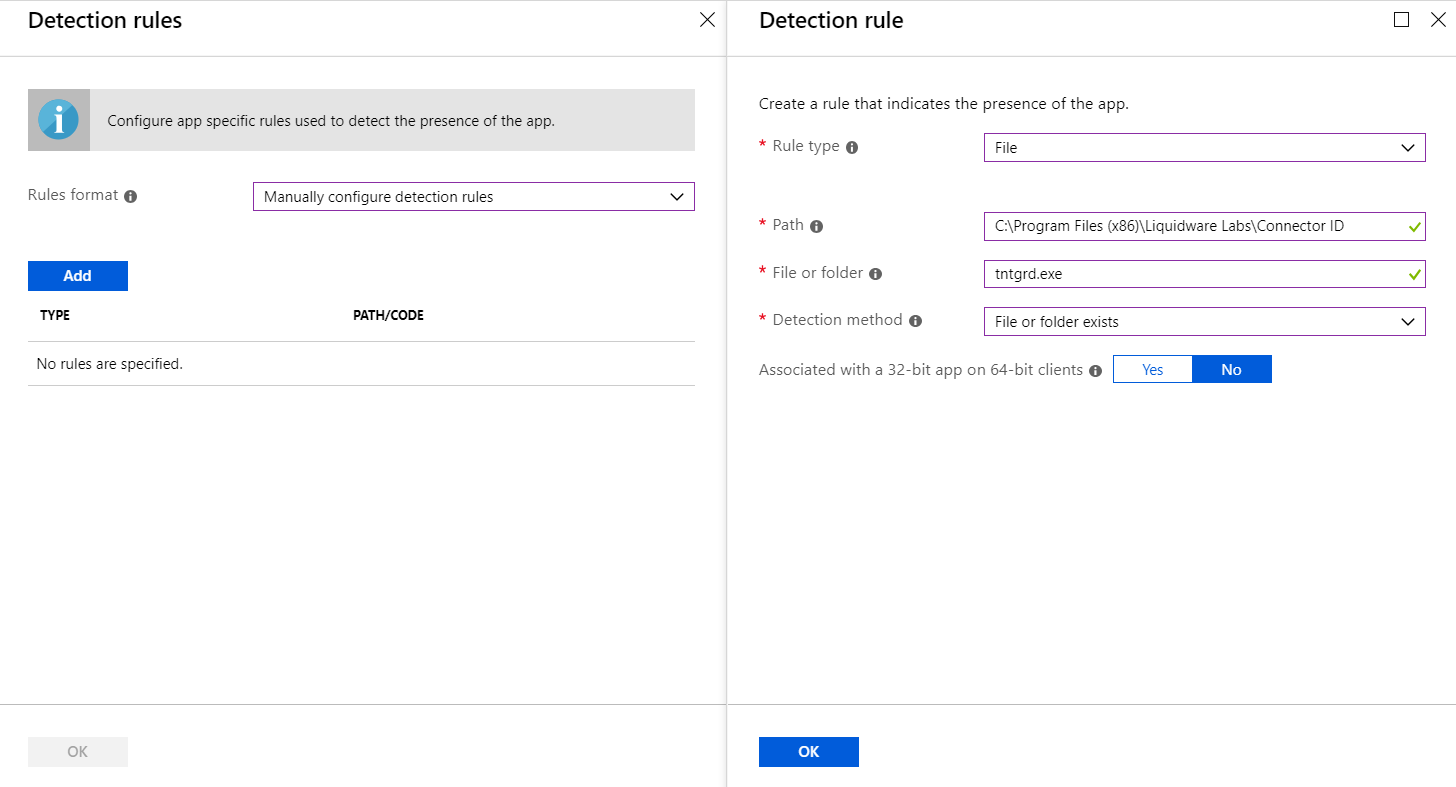
- You can set Return Codes and Tags but seeing as we can see the agent register correctly in the Hub Administrator console, we don’t need to. Once you are happy hit Add at the bottom!
- You will get a warning message saying your app isn’t ready yet, so this is a good time to go make a cup of tea 😊
- Got that tea (or coffee)? Great! Refresh the Intune page and you should now see the application is available and ready to be assigned!

- In the same window, select Assignments on the left-hand side and then Add Group.

- What you set next is very much dependant on your own configuration and which user groups you want the CID Key to be installed to. Personally, I would set the Assignment type to Required, as we don’t want manual intervention by our users, and we can just limit who we want to have it based on groups. I would also recommend hiding toast notifications as this again gives your end users one less thing to worry about. Below is an example configuration.

- Once done, hit Save and you are good to go.
- Now it’s time to test! Here we have our blank Windows 10 device with its first time sign in. Let’s sign in with an Azure AD User account that has the CID Key assigned.

- Completing the Windows 10 sign up, after logging in I can now see the CID Key has been successfully installed on my device, as this was pushed down in the background without any intervention by the end user.


- With that the deployment is complete.
I hope you can now see how easy it is to utilise Intune in this way and now that you are certain that all your devices will be supplied with the CID Key, you can start monitoring your end points and end user experience directly!








[…] Stratusphere UX is a great performance monitoring and user experience solution which also supports WVD. Other use cases for Stratuspehre include assessing your current desktop enterprise to idenfify Microsoft WVD candidates, performing an application assessment, and it can be used to help size your new environment accordingly. Stratusphere is domain independent so you can easily plan and scale your new deployment and inventories your current deployment, whether it’s WVD, On-Premise or BYOD devices. Read about deploying the StratusphereUX agent with Microsoft Intune here: https://blog.liquidware.com/2019/04/25/deploying-stratusphere-ux-connector-id-key-with-intune/ […]